Wednesday, 27 March 2013
Information Gathering : DNS Analysis
Hello guys, in this post i will try to gather information from websites with provided tools in backtrack. the target website is www.is2c-dojo.com and www.spentera.com. i will try the active and passive Information Gathering, and i will try to get information from that website as many as i can.
as we know, information gathering consist of two techniques, the passive information gathering and active information gathering . now let's get started.
Active information gathering
how can we get information if we just know the domain? firstly we can use nmap to get information about IP, operating system and open ports. general syntax for nmap : nmap [Scan Type(s)] [Options] {target specification}. let's give a try!
from the syntax above i can get the information about IP, OS version, firewall type, and open ports. now let's dig deeper into the system.
One of the valuable information in website is DNS, and i will try to get DNS information using dnsenum.
general syntax : dnsenum.pl [Options] <domain>
from dnsenum we obtained information about host addresses, name servers, and mail server.
not satisfied with the finding? now let's try one more tools, called dnsmap. dnsmap is a tool to get the IP addresses associated with a domain name. general syntax of dnsmap is : dnsmap <target-domain> [options].
now let's use dnsmap for is2c-dojo.com and spentera.com
Passive Information Gathering
there are numbers of technique for passive information gathering, but i only write about some of them. first tool that i use is "googling". i will input simple query to the google website and see how many results found.
the second tool that i will use is whois to obtain the informations legally provided for the domain name rental. she syntax is : whois <domain>. let's try in is2c-dojo.com and spentera.com.
i think that's enough for today's post, i will continue my writing about information security in the next time, and last but not least sorry for my bad english :)
as we know, information gathering consist of two techniques, the passive information gathering and active information gathering . now let's get started.
Active information gathering
how can we get information if we just know the domain? firstly we can use nmap to get information about IP, operating system and open ports. general syntax for nmap : nmap [Scan Type(s)] [Options] {target specification}. let's give a try!
nmap -O www.is2c-dojo.com
nmap -O www.spentera.com
from the syntax above i can get the information about IP, OS version, firewall type, and open ports. now let's dig deeper into the system.
One of the valuable information in website is DNS, and i will try to get DNS information using dnsenum.
general syntax : dnsenum.pl [Options] <domain>
./dnsenum.pl www.is2c-dojo.com
./dnsenum.pl www.spentera.com
from dnsenum we obtained information about host addresses, name servers, and mail server.
not satisfied with the finding? now let's try one more tools, called dnsmap. dnsmap is a tool to get the IP addresses associated with a domain name. general syntax of dnsmap is : dnsmap <target-domain> [options].
now let's use dnsmap for is2c-dojo.com and spentera.com
./dnsmap is2c-dojo.com
./dnsmap spentrea.com
Passive Information Gathering
there are numbers of technique for passive information gathering, but i only write about some of them. first tool that i use is "googling". i will input simple query to the google website and see how many results found.
site:is2c-dojo.com
found 516 results
site:spentera.com
found 317 results
the second tool that i will use is whois to obtain the informations legally provided for the domain name rental. she syntax is : whois <domain>. let's try in is2c-dojo.com and spentera.com.
whois is2c-dojo.com
whois spentera.com
i think that's enough for today's post, i will continue my writing about information security in the next time, and last but not least sorry for my bad english :)
Monday, 25 March 2013
indonesia cybercrime case : Shop owner arrested for cybercrime
The owner of a small computer shop in Mangga Dua shopping mall, Central Jakarta, was able to get through the electronic defense system of one of the city's major banks, police said Monday. The man, identified only as TL, entered fictitious credit card transactions into the system of the city's second largest bank in terms of assets, Bank Central Asia (BCA). The suspect did not use any sophisticated technology. He just used seven cards to authorize 12 transactions totaling Rp 425 million (US$). Most of the Visa and Mastercard cards were issued by foreign banks, including Prudential, Westpac and ANZ. Police suspect TL got the credit card numbers from recording the details of customers' past transactions, though there is also a possibility he broke into the bank's computer system. "He made all the transactions within an hour, which aroused the suspicions of BCA, as the card claimer," said the chief of the Jakarta Police's fiscal and monetary crimes unit, Adj. Sr. Comr. Aris Munandar. BCA later contacted the card holders, who are mostly non-nationals living abroad. They had no knowledge of the transactions. The bank canceled the transactions and reported the case to police in March. The suspect was arrested last week, police said. The vice chairman of the Indonesian Telecommunications Community, Mas Wigrantara, told The Jakarta Post that at least 1,000 incidents of e-banking fraud, virus uploads and hacking activities had been reported in the last six months. "Although the number is significant, banks are reluctant to report cases to police or the government because they are worried it will affect their reputation and the public will no longer trust e-banking," he said, adding that they preferred to report cases to their own security consultants. Wigrantara said the country already had the Indonesia Computer Security Incident Response Team, but it was not having much of an impact because of the limited number of cases reported to it. (Source)
hacking lab installation (windows xp in virtualbox) with backtrack
In my first post, i will give a little tutorials to install windows xp in virtualbox using backtrack 5. what is virtualbox? it's a general-purpose full virtualizer for x86 hardware, targeted at server, desktop and embedded use. you can get virtualbox for free in here.
i assume you have installed virtualbox in your operating system (in my case i am using backtrack 5 r3). now run the virtualbox application. firstly click new to begin create virtual OS and give name whatever you want and then click next.
after that give memory size for our virtual OS, just follow recommended setting (192 MB). and then click next
in this windows choose "create a virtual hard drive now" and then click create.
next in the hard drive file type choose the "VDI (virtualbox disk image) option.
next choose "dynamically allocated"
next determine the location of file and the size that will be used to store the virtual machine's data and then click create.
congratulations! we just finished the initial configuration!
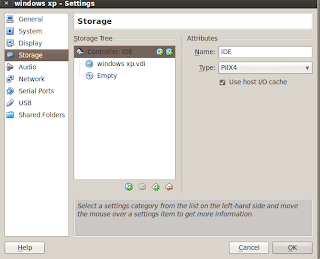
before we continue into booting mode, first we must configure booting option. click setting on the top-left menu. in system tab arrange boot order (make the harddisk in the first order) and in storage tab, specify the device that have installation image file or *.iso and then click ok. after we choose *.iso file, click start in main menu of virtualbox to begin installation.
the blue menu will show up and now we can install virtual XP like normal installation.
networking in virtualbox
in virtualbox there are 2 machine, host and guest. the host is the real machine and the guest is the virtual ones. both host and guest can communicate with each other.
connect host to guest and guest to host
in virtualbox menu click file -> preferences -> network and then create network interface and then press <space> to set IP and DHCP and then press OK.
after that click setting -> network and choose network adapter 1 to "host-only adapter" and press ok.
now let's run windows xp from virtualbox. go to command line and type "ipconfig" to view the ip of windows (guest).
as seen in screenshot the IP address is 192.168.56.101. to check whether host and guest are connected, open terminal in backtrack and type "ifconfig" to see the interface and IP address. the IP address host is 192.168.56.1.
now let's try to ping from host and guest and vice versa. turn off firewall on windows if the host can't ping guest.
BINGO! the host and guest are now connected!
connect guest to guest
basically, the method for connection between guest and guest are the same as method for host and guest. i'll write about it next time.
i assume you have installed virtualbox in your operating system (in my case i am using backtrack 5 r3). now run the virtualbox application. firstly click new to begin create virtual OS and give name whatever you want and then click next.
after that give memory size for our virtual OS, just follow recommended setting (192 MB). and then click next
in this windows choose "create a virtual hard drive now" and then click create.
next in the hard drive file type choose the "VDI (virtualbox disk image) option.
next choose "dynamically allocated"
next determine the location of file and the size that will be used to store the virtual machine's data and then click create.
congratulations! we just finished the initial configuration!
before we continue into booting mode, first we must configure booting option. click setting on the top-left menu. in system tab arrange boot order (make the harddisk in the first order) and in storage tab, specify the device that have installation image file or *.iso and then click ok. after we choose *.iso file, click start in main menu of virtualbox to begin installation.
the blue menu will show up and now we can install virtual XP like normal installation.
networking in virtualbox
in virtualbox there are 2 machine, host and guest. the host is the real machine and the guest is the virtual ones. both host and guest can communicate with each other.
connect host to guest and guest to host
in virtualbox menu click file -> preferences -> network and then create network interface and then press <space> to set IP and DHCP and then press OK.
after that click setting -> network and choose network adapter 1 to "host-only adapter" and press ok.
now let's run windows xp from virtualbox. go to command line and type "ipconfig" to view the ip of windows (guest).
as seen in screenshot the IP address is 192.168.56.101. to check whether host and guest are connected, open terminal in backtrack and type "ifconfig" to see the interface and IP address. the IP address host is 192.168.56.1.
now let's try to ping from host and guest and vice versa. turn off firewall on windows if the host can't ping guest.
connect guest to guest
basically, the method for connection between guest and guest are the same as method for host and guest. i'll write about it next time.
Subscribe to:
Comments (Atom)